A little less conspicuous - Part 4: Obscuring DNS traffic
This is the final follow-up article for A little less conspicuous - Part 1: Introduction. Please read that first, if you came here through a direct link.
Also it is recommended to read the previous parts of the series as well, before reading this post.
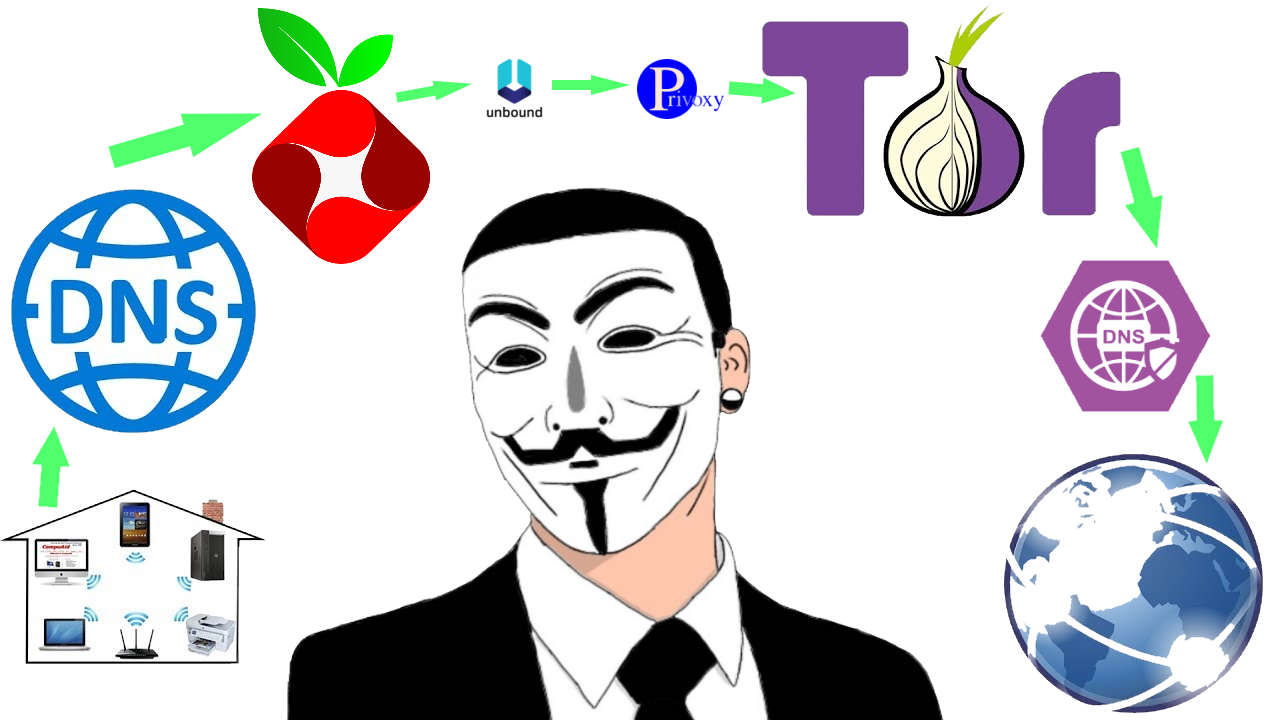
You have come to the pinnacle of this series and we are now going to tie together all that you have learned in previous episodes.
While using the Pi-hole DNS Server (Part 2) and the Tor Proxy (Part 3) separately is totally valid, why not go the extra mile and fully secure and anonymize your DNS traffic on a permanent basis and at the same time configure your Tor Browser (Download) to use your Tor Proxy and the Pi-hole together.
“Why go through all this trouble to hide only this specific (DNS) portion of my traffic?” you might ask. I will just have to refer you to the title and opening statement in Part 1 of this series. Be ‘A little less conspicuous’ and ‘It really wouldn’t harm you, or anyone for that matter and makes just plain sense.’
Nonetheless, we can say that the general security, privacy and even anonymity level of at least some of your internet interactions will be raised by using a permanent DNS-over-TLS-over-Tor (DoToT) set-up on your local network. Also you have the option to totally ‘emerge’ yourself by using the Tor Browser configured with your Tor Proxy.
And now for something very important…
![]() Disclaimer
Disclaimer
This article and follow-ups have no ambitions to totally anonymize anyone on the internet, but just to make it a little bit more difficult for certain parties (ie. ISP’s, governments, advertising moguls and the likes) to track you or your small company.
The proposed setup is meant for demo purposes only and is certainly not production-ready without extra precautions and explanations put in place.
The packages, distributions and commands used and referred to in this article are valid for the most recent software versions available at the date of article publication. There is no guarantee the routines and packages described here will keep working at a later date.
Furthermore rest assured, since the internet (no capital here!) was created with absolutely no security or privacy in mind, it will never deliver on any promise of these concepts. But why hand-over all your data on a platter and be profiled? It’s like peeing naked in the middle of Grand Central Station and have everyone stare at you, would you really? At least put on a dress and pee in a bucket underneath you, doing that some people won’t even notice you are there.
This article is here to provide you a bucket. Please bring your own dress.
Machine variables
The following variables will be used in the guidance offered by this article.
The names of the machines have already been used in Part 2 and 3 of this series to set-up the individual machines.
| Variable | Example Value |
|---|---|
| ServerName1 | DNS-V1-01 |
| ServerIP1 | 192.168.0.50 |
| ServerName2 | TOR-V1-01 |
| ServerIP2 | 192.168.0.51 |
| ExistingADDomain | mydomain.local |
| ExistingADDomainDNSServer | 192.168.0.10 |
Setting up DNS-over-TLS-over-Tor (DoToT)
Please refer to the red textual markings in the architecture diagram laid out in Part 1 of this series to get a grip on what you are trying to achieve.
- Configure DietPi Software:
- On DNS-V1-01
- Read the article: DNS over TLS and TOR with Pi-Hole as a reference, but substitute ‘stubby’ with ‘unbound’
- Login to your machine as
root - Install ProxyChains:
sudo apt-get install proxychains-
ProxyChains (wrapping specific programs to use a proxy)
- Change the default config as follows:
sudo nano /etc/proxychains.conf- Comment out the line
proxy_dnsso that it appears like this:# proxy_dns - At the end of the file replace the line starting with
socks4withhttp 192.168.0.51 9051
- Comment out the line
- Check the workings (Should return different IP addresses):
proxychains curl ifconfig.mecurl ifconfig.me
- Change the default config as follows:
-
ProxyChains (wrapping specific programs to use a proxy)
- Reconfigure Unbound (to use ProxyChains)
-
Unbound (Recursive Caching DNS Server)
- Stop the Unbound service
sudo systemctl stop unbound.service
- Change the unbound config so it starts up through ProxyChains
-
sudo nano /etc/systemd/system/multi-user.target.wants/unbound.service- Change the ExecStart line to be
ExecStart=/usr/bin/proxychains /usr/bin/unbound -d -p $DAEMON_OPTS
- Change the ExecStart line to be
-
- Speed up regular performance by upping the TTL for Unbounds cached DNS entries
-
sudo nano /etc/unbound/unbound.conf.d/dietpi.conf- Change the line starting with
cache-min-ttltocache-min-ttl 3500
- Change the line starting with
-
- Check unbound config
-
unbound-checkconf(Should return no errors)
-
- Start the unbound service
sudo systemctl start unbound.service
- Stop the Unbound service
-
Unbound (Recursive Caching DNS Server)
- Check full workings
- First execution should take several seconds, Second execution should return instantly:
dig @127.0.0.1 -p 5335 google.todig @127.0.0.1 -p 5335 google.to
-
dietpi-services- Status -> Log should show connections to 192.168.0.51
- First execution should take several seconds, Second execution should return instantly:
- On TOR-V1-01
- Login to your machine as
root - Reconfigure Privoxy
-
Privoxy (HTTP Proxy)
- Replace the following line in the default config file (
sudo nano /etc/privoxy/config)…
1 2
# forward to Tor (mind the dot at the end!) forward-socks5 / 127.0.0.1:9050 .
- …with the following
1 2 3 4 5 6 7
## forward to Tor, but forward DNS traffic to Pi-hole (mind the dots at the end of each line!) forward-socks4 / 127.0.0.1:9050 . # HTTP traffic goes through Tor, no DNS handling forward-socks4 :443 127.0.0.1:9050 . # HTTPS traffic goes through Tor, no DNS handling forward-socks4 :853 127.0.0.1:9050 . # TLS traffic goes through Tor, no DNS handling forward-socks4 :53 192.168.0.50:53 . # DNS traffic is forwarded to local DNS (Pi-hole) forward-socks4a .onion 127.0.0.1:9050 . # .onion domains go through Tor forward-socks4a .exit 127.0.0.1:9050 . # .exit domains go through Tor
- This configuration will make sure that you effectively create your own controlled version of a ‘DNS leak’, but since all DNS traffic (except request for the obvious Tor hidden services: .onion and .exit) will be forwarded from the Pi-hole to our Unbound forwarders using TLS, which will in turn be forwarded through Tor as well, this potential leak is remediated. The target DNS resolvers (configured in Unbound) will not be able to track you.
- Replace the following line in the default config file (
reboot
-
Privoxy (HTTP Proxy)
- Check full workings
- Run
ss- Connections from 192.168.0.50 should be present
- Run
- Login to your machine as
- Configure owned LAN/WAN services and devices
-
Recommended: On any networked client with the Tor Browser:
- Download this zip file to employ Firefox Auto Configuration for the Tor Browser.
- Read the ‘Instructions.txt’ file in the zip file and place the mentioned packed files in their proper locations.
- IMPORTANT: You might need to edit the ‘firefox.cfg’ file and amend the IP addresses used for the Tor Proxy (multiple places)
- Open the Tor Browser
- Surf to: DuckDuckGo .onion and DuckDuckGo ‘regular’. Both should resolve correctly
- Fantastic! You now have effectively disabled the Tor Browser built-in SOCKS5 Proxy and replaced it with your own Tor Proxy keeping all other Tor Browser default secure settings and extensions in place, additionally all DNS traffic is being routed through your Pi-hole first, before being resolved through Tor.
- Optional, but recommended: Disable ‘Outgoing WAN connections’ using ports 53 and 853 (TCP/UDP) for all devices on your network in your firewall.
- Since we now send all DNS traffic to the Pi-hole and unknown domains will get forwarded as TLS traffic over Tor by the ProxyChains + Unbound set-up, outgoing DNS ports are not used anymore on your network and can thus be blocked.
- NOTE: Maybe have a single machine exception in your firewall, in case any one of your machines (DNS-V1-01 and TOR-V1-01) ‘die’ on you.
-
Recommended: On any networked client with the Tor Browser:
- On DNS-V1-01
On any Tor Proxy connected machine in your network, check if your DNS Configuration works correctly:
- => https://dnsleaktest.com
- Check against DNS-leaks and what DNS-server you currently use, these should be the ones configured as resolvers in Unbound
- => https://cmdns.dev.dns-oarc.net
- Check your DNS features
- => http://www.dnssec-or-not.com
- If you use DNSSEC
- => https://tools.dnsstuff.com
- DNS-Tools and more
![]() Congratulations
Congratulations
You now have successfully configured a DNS-over-TLS-over-Tor chain and your networked devices/browsers that were already configured to use the Pi-hole DNS server will automatically start using this configuration! Furthermore if you use your Tor Proxy actively all DNS traffic will be routed to ypur Pi-hole before entering the Tor network for resolving as already encrypted TLS traffic.
This marks the end of this series, I hope you found it useful.
The end
This series comprises of 4 parts:
- Part 1: A little less conspicuous - Introduction
- Part 2: A little less conspicuous - The DNS Sinkhole on running your own DNS Pi-hole with secure Admin WebUI + Unbound + TLS resolvers on DietPi
- Requirements: None, can run Standalone
- Achieves: General Ad blocking for your network + Obscure DNS traffic for your ISP by using DNS-over-TLS resolvers
- Part 3: A little less conspicuous - The Tor Proxy on running your own Tor SOCKS5 Proxy + Privoxy HTTP Proxy on DietPi
- Requirements: None, can run Standalone
- Achieves: Have the option to ‘go anonymous’ on the web when you want it, also for mobile devices (iOS, Android)
-
This post - Part 4: A little less conspicuous - Obscure DNS traffic on routing your DNS Traffic through Tor
- Requirements: Parts 2 and 3
- Achieves: Obscure already Secure DNS-over-TLS Traffic from your DNS resolvers + Use Tor Browser and Pi-hole together
